As part of system-wide efforts to address the increasing threats to the security of our information systems and data, a comprehensive security awareness campaign is being rolled by our IT Department. Each member of the MVC community has a responsibility to safeguard the information assets entrusted to us.
Cyber Security Awareness Training
What’s at stake?
By tricking campus users into giving away their information, attackers can:
- Steal money from victims
- Perform identity theft
- Send spam from compromised email accounts
-
Use your credentials to access other campus systems, attack other systems, steal confidential data, and jeopardize the mission of the campus
These things really do happen, and happen far too often.
What to look for?
Phishing scams
Phishing is a type of attack carried out in order to steal usernames, passwords, credit card information, Social Security Numbers, and other sensitive data by masquerading as a trustworthy entity. Phishing is most often seen in the form of malicious emails pretending to be from credible sources such as MVC departments or financial organizations/vendors related to the college.
Most commonly, a phishing scam is initiated by an email that has the appearance of official business, requesting that you perform an urgent action, such as logging into your account to confirm your password.
The email will often contain a link to a fraudulent login page, where your credentials are captured for future compromise. Or the link takes you to a web page where malicious code is silently installed on your system to capture your credentials.
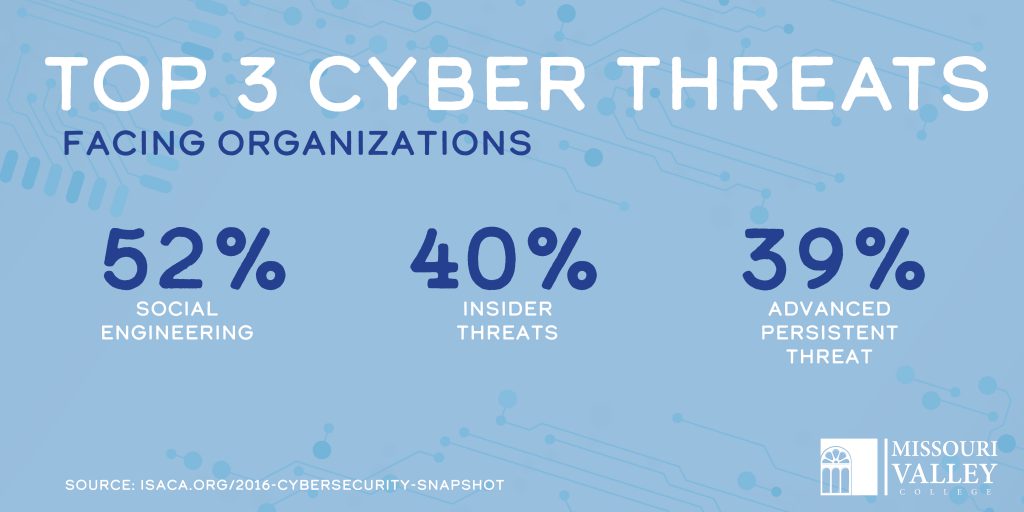
Social Engineering
Social engineering is the art of manipulating people so they give up confidential information. Criminals use social engineering tactics because it is usually easier to exploit your natural inclination to trust than it is to discover ways to hack your software. For example, it is much easier to fool someone into giving you their password than it is for you to try hacking their password (unless the password is really weak).
Dictionary or Brute-Force attacks
Dictionary attacks are a technique of breaking into an account by guessing a passphrase from the dictionary, or a list of commonly used passwords. Also know as a “brute-force attack”, passphrases that are poorly generated are the most susceptible (e.g., passphrases containing common words, pet’s name, etc.).
Using Public Kiosks or other untrusted devices
Your credentials are at especially high risk when you enter them on untrusted devices such as:
- Public kiosks or terminals (e.g. hotels, libraries, airports, coffee shops)
- Borrowing a friend or colleague’s computer or mobile device
These untrusted devices may have already been compromised by malware installed to capture your credentials. And if you forget to properly logout and close the web browser, someone can hijack your account afterwards.
Shoulder Surfing
A technique whereby the attacker simply observes someone while they type their passphrase. Shoulder Surfing is especially a risk in libraries, computer labs and other public areas.
Other techniques include…
- Hackers that have successfully stolen credentials from one website will attempt to use them on other sites, exploiting the fact that many victims reuse passphrases across multiple systems.
- Hackers will often install software or hardware devices known as “keyloggers” to capture the input from the keyboard.
- Attackers can intercept credentials by monitoring unencrypted network traffic (also known as “sniffing”). This happens most often on open wireless networks and when credentials are sent in clear text through email or unsecured web connections (e.g., URL links beginning with http:// instead of https://).